There is a wonderful blog on Fusion Security by Jani Rautiainen. People who are from EBS background will be able to connect EBS security with FA security. Only thing they have to know which terminology maps to what.
If you are from EBS background you know that security is handled through Functions, Menus, Responsibilities, Users and Profile Values, Request Groups, Data Groups and in some cases (Purchasing, Shipping etc) the inbuilt logic.
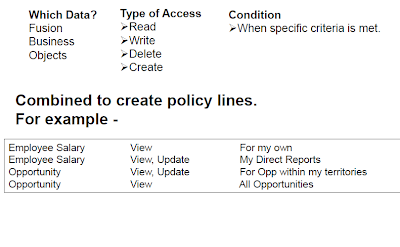
Where as in Fusion the access is fully controlled by RBAC (Role Based Access Control). The concept is very simple 'WHO can do WHAT on WHICH set of data'
Here WHO is user who has been assigned a set of roles, e.g. SHEIKHM is the user who has been assigned roles
You can log on to OIM with your user to access Oracle Identity Manager - Self Service Page. Click on My roles and you will see the list of roles assigned to you. If you have OIMADMIN privileges which is basically the IDM Administrators role, then you can add remove roles from users.
'WHAT' is Duties/Privileges under the Roles
What also determines what menu items will appear under Navigator and what Tasks the user will be able see from the Task Panes.
'WHICH' is basically Data Security and it determines what data you will see on the screen.
In EBS we setup users from System Administrator Responsibility - > Security - > Users
There we create user credentials and assign list of responsibilities. In Fusion this is done in OID and the same is managed through OIM (if customer has not used any other third party LDAP store for identity).
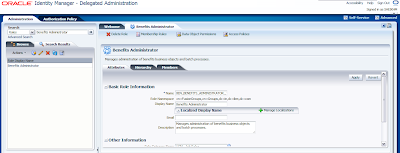
To do this navigate to Oracle Identity Manager - Delegated Administration and then click on Administration link placed at the top right hand side and click on Create User
Once you have entered the user details and clicked Save, the Role Provisioning screen will appear where you will specify roles the user will be provided. In EBS we have Function or Menu exclusion provisions. But here in Fusion I believe we don't have that till now. Though it is not recommended to create Application Users from OIM except for initial implementation users, but still we need to know how these Middleware Components fit into overall architecture. Use HCM Role Mapping Rules to automatically assign roles when they are created through any interface like FBL or HR2HR.
In EBS the menu, the user will see is determined by Responsibility Definition. There we specify the menus and their sequences. The menus consist of Sub-menus or Functions. The function may call Oracle Form, SRS screen or OAF page. Where as in Fusion the Applications UI has been built using ADF and the security has been incorporated there itself. The pages, regions, Task Flows, menus, Dashboards etc are protected using Security Context. The Security Context is provided by Oracle Platform Security Services(OPSS).
Oracle Fusion Applications designers leverage the Oracle Platform Security Services (OPSS) framework through Oracle JDeveloper security wizards.
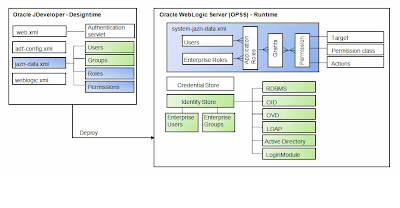
As shown in Figure OPSS is the security foundation for Oracle Fusion Middleware: all Oracle Fusion Middleware components and Oracle Fusion Applications “consume” the OPSS framework’s services.
OPSS is a self-contained, portable environment that runs on an application server such as Oracle WebLogic Server. If you are familiar with ADF you know that at development time, OPSS services are directly invoked from the development environment (Oracle JDeveloper) through wizards. When the application is deployed to the runtime environment, systems and security administrators can access OPSS services for configuration purposes through Oracle Enterprise Manager Fusion Middleware (FMW) Control, command line tools such as WebLogic Scripting Tool (WLST), and more specifically Oracle Authorization Policy Manager (APM).
This figure shows you design time OPSS and Run Time OPSS. Let me go to one step down to show you how security is configured in ADF
Some Application Roles are created in ADF because the framework Supports security for Resource Type as Task Flow, Pages, Regions, ADF Methods etc. Some of them are incorporated in the logic itself. now the question is How will I know what are the roles that are shipped with the respective applications
Let's see them for HcmPayrollApp under HCM Product Family.
Log on to you HCM Domain Enterprise Manager Fusion Applications Control.
Expand Oracle Fusion Human Capital Management --> Fusion Applications --> HcmPayrollApp
Then select HcmPayrollApp
This is the screen which you will see after the selection. Now to see the Shipped Application Roles. To get that navigate to the pages as shown in the next picture
One you do that the next screen will show you all the application roles and their associated external role mapping
Once you do that you will see the location of the policy store provider and the list of application roles (These are basically duty roles).
If you select any of the roles and click on edit you will see the mapping with other Application or External Roles as shown in the next picture
Now if you log on to Oracle Authorization Policy Manager (APM) to see the list of entitlements and associated grants for the Roles you will have the clear understanding. APM is a graphical user-interface console for managing OPSS-based authorization policies. APM was specifically designed to support Oracle Fusion Applications’ security policies using a centrally managed approach. APM is designed for customers relying on Oracle Fusion Middleware products consuming OPSS services, such as Oracle Fusion Applications, or OPSS used by in-house custom applications.
Here our aim will be to see how the ADF resources are secured and how to view this configuration. So let's take BEN_BENEFITS_SETUP_DUTY for this case study. In APM when you log on you will see the screen as below
At the Top Left you will see a section called Search. Select For Application Roles in hcm and search for BEN_BENEFITS_SETUP_DUTY
and click GO
This is what you will see when you search. Click on Open. It you show the details of the Application Role - Application Role Hierarchy, External Role Mapping & External User Mapping. As you can see from the next screen that BEN_BENIFITS_SETUP_DUTY role has been mapped to Benefits Administrator and Benefits Manager Roles created in your LDAP Identity store. The next picture from OIM confirms that
I logged on to OIM and searched the Job Role which is nothing but External Role created in OID. Now let's go back to APM and try to see the Authorization Policies for our DUTY Role
So after opening the Application Role click on Find Policies at the top right hand side. This will show the Authorization Policy. Now as can be seen from the picture that there are two tabs Function Security and Data Security Policies.
Function Security decides the access to UI where as Data Security decides the data you will see on the screen. So let's see what the user assigned with this role (though Duty roles are not directly assigned to users but for the sake of understanding let's assume that this has been done).
By default Function Security Tab is automatically selected when you open Authorization Policy.
Here you see that there is one Function Security Policy has been specified and that is basically Entitlement Set. Now click on Open you will see list of Entitlements. Entitlements are nothing but group of Resources and corresponding Actions that can be performed on those. The following picture will show those.
Click on the info button and you will see the Entitlement Name. Now to see what all the resources (UI, Task Flows) that can be accessed through this role. Let's search this Entitlement.
This screen specifies that the user who has been assigned this role directly or indirectly will be able to access the Task Flows as mentioned, e.g - PlanEnrollmentFlow and Page e.g - PlanDIConfirmationPageDef
In OPSS, the pages are defined as resource and they are specified as shown in the picture.
So this explains the way the UIs are secured in Fusion Applications. I will show how Data Security Policies are specified in the following posts.
Cheers......................
If you are from EBS background you know that security is handled through Functions, Menus, Responsibilities, Users and Profile Values, Request Groups, Data Groups and in some cases (Purchasing, Shipping etc) the inbuilt logic.
Where as in Fusion the access is fully controlled by RBAC (Role Based Access Control). The concept is very simple 'WHO can do WHAT on WHICH set of data'
Here WHO is user who has been assigned a set of roles, e.g. SHEIKHM is the user who has been assigned roles
You can log on to OIM with your user to access Oracle Identity Manager - Self Service Page. Click on My roles and you will see the list of roles assigned to you. If you have OIMADMIN privileges which is basically the IDM Administrators role, then you can add remove roles from users.
'WHAT' is Duties/Privileges under the Roles
What also determines what menu items will appear under Navigator and what Tasks the user will be able see from the Task Panes.
'WHICH' is basically Data Security and it determines what data you will see on the screen.
In EBS we setup users from System Administrator Responsibility - > Security - > Users
There we create user credentials and assign list of responsibilities. In Fusion this is done in OID and the same is managed through OIM (if customer has not used any other third party LDAP store for identity).
To do this navigate to Oracle Identity Manager - Delegated Administration and then click on Administration link placed at the top right hand side and click on Create User
Once you have entered the user details and clicked Save, the Role Provisioning screen will appear where you will specify roles the user will be provided. In EBS we have Function or Menu exclusion provisions. But here in Fusion I believe we don't have that till now. Though it is not recommended to create Application Users from OIM except for initial implementation users, but still we need to know how these Middleware Components fit into overall architecture. Use HCM Role Mapping Rules to automatically assign roles when they are created through any interface like FBL or HR2HR.
In EBS the menu, the user will see is determined by Responsibility Definition. There we specify the menus and their sequences. The menus consist of Sub-menus or Functions. The function may call Oracle Form, SRS screen or OAF page. Where as in Fusion the Applications UI has been built using ADF and the security has been incorporated there itself. The pages, regions, Task Flows, menus, Dashboards etc are protected using Security Context. The Security Context is provided by Oracle Platform Security Services(OPSS).
Oracle Fusion Applications designers leverage the Oracle Platform Security Services (OPSS) framework through Oracle JDeveloper security wizards.
As shown in Figure OPSS is the security foundation for Oracle Fusion Middleware: all Oracle Fusion Middleware components and Oracle Fusion Applications “consume” the OPSS framework’s services.
OPSS is a self-contained, portable environment that runs on an application server such as Oracle WebLogic Server. If you are familiar with ADF you know that at development time, OPSS services are directly invoked from the development environment (Oracle JDeveloper) through wizards. When the application is deployed to the runtime environment, systems and security administrators can access OPSS services for configuration purposes through Oracle Enterprise Manager Fusion Middleware (FMW) Control, command line tools such as WebLogic Scripting Tool (WLST), and more specifically Oracle Authorization Policy Manager (APM).
This figure shows you design time OPSS and Run Time OPSS. Let me go to one step down to show you how security is configured in ADF
Some Application Roles are created in ADF because the framework Supports security for Resource Type as Task Flow, Pages, Regions, ADF Methods etc. Some of them are incorporated in the logic itself. now the question is How will I know what are the roles that are shipped with the respective applications
Let's see them for HcmPayrollApp under HCM Product Family.
Log on to you HCM Domain Enterprise Manager Fusion Applications Control.
Expand Oracle Fusion Human Capital Management --> Fusion Applications --> HcmPayrollApp
Then select HcmPayrollApp
This is the screen which you will see after the selection. Now to see the Shipped Application Roles. To get that navigate to the pages as shown in the next picture
One you do that the next screen will show you all the application roles and their associated external role mapping
Once you do that you will see the location of the policy store provider and the list of application roles (These are basically duty roles).
If you select any of the roles and click on edit you will see the mapping with other Application or External Roles as shown in the next picture
Now if you log on to Oracle Authorization Policy Manager (APM) to see the list of entitlements and associated grants for the Roles you will have the clear understanding. APM is a graphical user-interface console for managing OPSS-based authorization policies. APM was specifically designed to support Oracle Fusion Applications’ security policies using a centrally managed approach. APM is designed for customers relying on Oracle Fusion Middleware products consuming OPSS services, such as Oracle Fusion Applications, or OPSS used by in-house custom applications.
Here our aim will be to see how the ADF resources are secured and how to view this configuration. So let's take BEN_BENEFITS_SETUP_DUTY for this case study. In APM when you log on you will see the screen as below
At the Top Left you will see a section called Search. Select For Application Roles in hcm and search for BEN_BENEFITS_SETUP_DUTY
and click GO
This is what you will see when you search. Click on Open. It you show the details of the Application Role - Application Role Hierarchy, External Role Mapping & External User Mapping. As you can see from the next screen that BEN_BENIFITS_SETUP_DUTY role has been mapped to Benefits Administrator and Benefits Manager Roles created in your LDAP Identity store. The next picture from OIM confirms that
I logged on to OIM and searched the Job Role which is nothing but External Role created in OID. Now let's go back to APM and try to see the Authorization Policies for our DUTY Role
So after opening the Application Role click on Find Policies at the top right hand side. This will show the Authorization Policy. Now as can be seen from the picture that there are two tabs Function Security and Data Security Policies.
Function Security decides the access to UI where as Data Security decides the data you will see on the screen. So let's see what the user assigned with this role (though Duty roles are not directly assigned to users but for the sake of understanding let's assume that this has been done).
By default Function Security Tab is automatically selected when you open Authorization Policy.
Here you see that there is one Function Security Policy has been specified and that is basically Entitlement Set. Now click on Open you will see list of Entitlements. Entitlements are nothing but group of Resources and corresponding Actions that can be performed on those. The following picture will show those.
Click on the info button and you will see the Entitlement Name. Now to see what all the resources (UI, Task Flows) that can be accessed through this role. Let's search this Entitlement.
This screen specifies that the user who has been assigned this role directly or indirectly will be able to access the Task Flows as mentioned, e.g - PlanEnrollmentFlow and Page e.g - PlanDIConfirmationPageDef
In OPSS, the pages are defined as resource and they are specified as shown in the picture.
So this explains the way the UIs are secured in Fusion Applications. I will show how Data Security Policies are specified in the following posts.
Summary
Fusion Applications has been developed using ADF where the security has been introduced decoratively using OPSS APIs which are then deployed in Weblogic Domains and is then configured there by Security Administrator using Graphical Tool APM. At run time ADF delegates authentication and authorization to OPSS which then uses OID or any LDAP Identity and Policy store to get the details of roles and privileges the user has and accordingly access is granted.Cheers......................


















Hi Mehabub,
ReplyDeleteGreat article, you have very easly related EBS & fusion security in a single page.
Thanks,
Sanjay
Nice article... Keep it up.
ReplyDeleteDakshesh Patel
Good one
ReplyDelete